Let’s get a quick overview of Server Side vs Client Side Encryption for Amazon S3 using KMS.
You will learn
- What is Server Side Encryption?
- What is Client Side Encryption?
- How can you implement Encryption for S3 using KMS?
- When do we use Server Side vs Client Side Encryption?
KMS and Cloud HSM
![]()
![]()
- How do you generate, store, use and replace your keys?
- AWS provides two important services - KMS and Cloud HSM
- Manage your keys
- Perform encryption and decryption
AWS KMS
![]()
- Create and manage cryptographic keys (symmetric and asymmetric)
- Control their use in your applications and AWS Services
- Define key usage permissions (including cross account access)
- Track key usage in AWS CloudTrail (regulations & compliance)
- Integrates with almost all AWS services that need data encryption
- Automatically rotate master keys once a year
- No need to re-encrypt previously encrypted data (versions of master key are maintained)
- Schedule key deletion to verify if the key is used
- Mandatory minimum wait period of 7 days (max-30 days)
Server Side Encryption
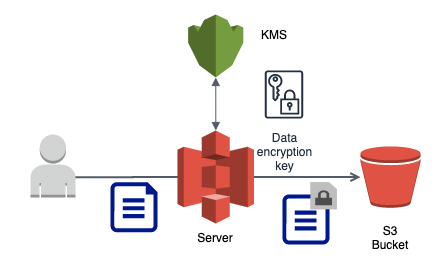
- Client sends data (as is) to AWS service
- AWS service interacts with KMS to perform encryption on the server side
- Recommended to use HTTPS endpoints to ensure encryption of data in transit
- All AWS services (including S3) provides HTTPS endpoints
- Encryption is optional with S3 but highly recommended in flight and at rest
Server Side Encryption - S3
![]()
![]()

![]()
- SSE-S3:
- AWS S3 manages its own keys
- Keys are rotated every month
- Request Header - x-amz-server-side-encryption(AES256)
- SSE-KMS:
- Customer manages keys in KMS
- Request Headers - x-amz-server-side-encryption(aws:kms) and x-amz-server-side-encryption-aws-kms-key-id(ARN for key in KMS)
- SSE-C:
- Customer sends the key with every request
- S3 performs encryption and decryption without storing the key
- HTTPS is mandatory
Client Side Encryption
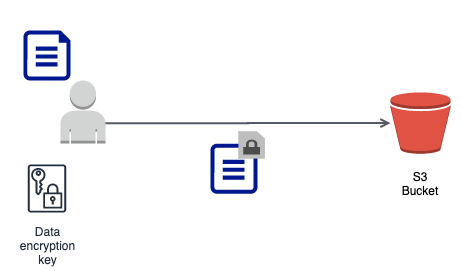
- Client manages encryption process and sends encrypted data to AWS service
- AWS will not be aware of master key or data key
- AWS service stores data as is
- For Amazon S3, you can use a client library (Amazon S3 Encryption Client)